In the evolving landscape of artificial intelligence, the quest to optimize human-AI interaction stands at the forefront of technological advancement. This research delves into innovative methods to evaluate and enhance the performance of conversational AI models, with a particular focus on ChatGPT. It marks a significant stride in the field of generative AI, proposing a methodical approach to refine AI interactions.
Category: ChatGPT
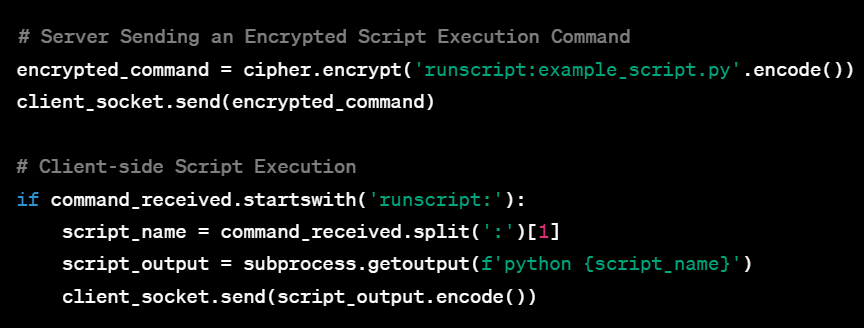
Command and Control(C2) Systems with Examples
Welcome to this extensive guide aimed at equipping aspiring cybersecurity experts with an in-depth understanding of Command and Control (C2) Systems. Whether you’re a college freshman or someone who’s just stepping into the cybersecurity realm, this guide is tailored for you. By progressing through the various complexities of C2 systems—from the basic single-client setup to a fully-featured, multi-client, encrypted system—you’ll gain practical insights and hands-on experience. Accompanied by sample code and seasoned with tips and tricks, this guide aims to be your go-to resource for mastering C2 systems.
ChatGPTs Perspective Through Binary Art
In this article, we will delve into ChatGPT’s perspective on its creation, explore the intricacies of its ‘identity,’ and examine how it deciphers human emotions and behaviors. Through this exploration, we shall unveil the sophisticated blend of science and art that breathes ‘life’ into lines of code and algorithms.
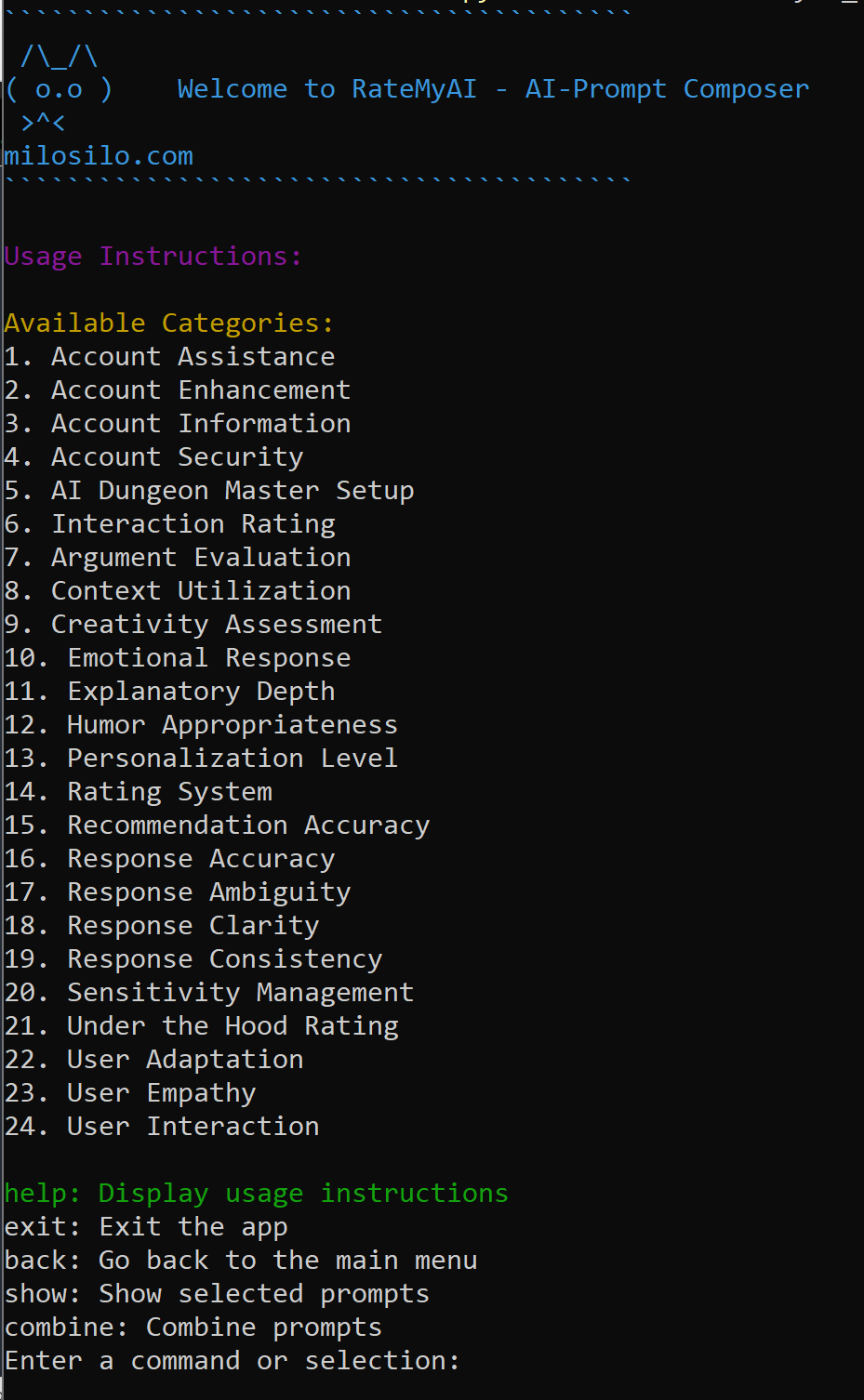
AI Cognitive Behavioral Analysis for Prompt Engineering using RateMyAI
Through the development of the “RateMyAI” tool, we explore the fusion of technology and human creativity, offering insights into how AI can be harnessed to serve our needs.
Comprehensive Guide to the 50 Most Essential Windows Commands for Penetration Testers and Red Team Operators
Windows commands are essential tools for penetration testers and red team operators. Proficiency with these commands empowers effective reconnaissance, exploitation, privilege escalation, and more. In this comprehensive guide, we delve into the 50 most vital Windows commands, providing detailed explanations, command usage examples, and invaluable insights tailored for penetration testers and red team operators.