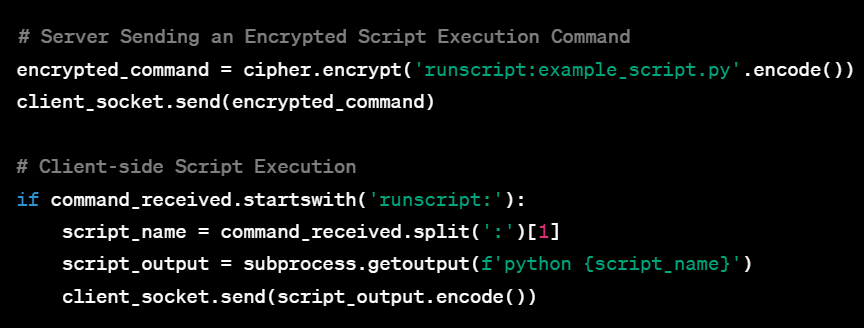
Welcome to this extensive guide aimed at equipping aspiring cybersecurity experts with an in-depth understanding of Command and Control (C2) Systems. Whether you’re a college freshman or someone who’s just stepping into the cybersecurity realm, this guide is tailored for you. By progressing through the various complexities of C2 systems—from the basic single-client setup to a fully-featured, multi-client, encrypted system—you’ll gain practical insights and hands-on experience. Accompanied by sample code and seasoned with tips and tricks, this guide aims to be your go-to resource for mastering C2 systems.
Tag: Penetration Testing
Hack Hard: A Classic RPG Hacking Game
PLAY IT NOW: https://github.com/milosilo/hack_hard Description:Step into a world where cyber challenges meet the spirit of a retro RPG in “Hack Hard.” This immersive experience takes you on a nostalgic journey inspired by the legendary John McClane. As a savvy hacker, you’ll navigate through virtual skyscrapers filled with hacking quests, each floor bringing new challenges and… Continue reading Hack Hard: A Classic RPG Hacking Game
AI Cognitive Behavioral Analysis for Prompt Engineering using RateMyAI
Through the development of the “RateMyAI” tool, we explore the fusion of technology and human creativity, offering insights into how AI can be harnessed to serve our needs.
Guide to Penetration Testing on AI Systems
n the realm of artificial intelligence (AI), safeguarding the security of AI systems has become an indispensable endeavor. Conducting penetration testing on these systems introduces a multifaceted challenge due to their intricate architecture and dynamic nature. This all-encompassing guide takes you through intricate methodologies, advanced tools, and real-world examples essential for performing thorough penetration testing on AI systems. The ultimate objective? To fortify these systems against the ever-evolving and diverse landscape of cyber threats.
Comprehensive Guide to Essential Penetration Testing Tools for Each Assessment Stage
Penetration testing is a dynamic process that encompasses various stages, each demanding a specific arsenal of tools. This guide presents a comprehensive compilation of essential tools for every stage, offering in-depth explanations, detailed usage examples, and strategic insights. Equip yourself with these powerful tools to enhance your penetration testing capabilities and conduct thorough assessments that simulate real-world cyber threats effectively.