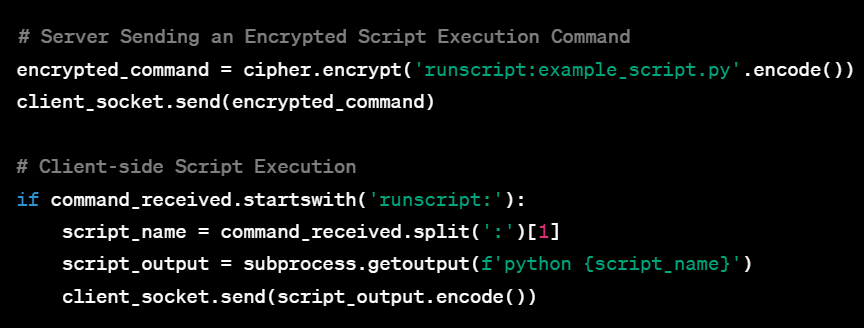
Welcome to this extensive guide aimed at equipping aspiring cybersecurity experts with an in-depth understanding of Command and Control (C2) Systems. Whether you’re a college freshman or someone who’s just stepping into the cybersecurity realm, this guide is tailored for you. By progressing through the various complexities of C2 systems—from the basic single-client setup to a fully-featured, multi-client, encrypted system—you’ll gain practical insights and hands-on experience. Accompanied by sample code and seasoned with tips and tricks, this guide aims to be your go-to resource for mastering C2 systems.
Tag: oscp
Comprehensive Guide to Essential Penetration Testing Tools for Each Assessment Stage
Penetration testing is a dynamic process that encompasses various stages, each demanding a specific arsenal of tools. This guide presents a comprehensive compilation of essential tools for every stage, offering in-depth explanations, detailed usage examples, and strategic insights. Equip yourself with these powerful tools to enhance your penetration testing capabilities and conduct thorough assessments that simulate real-world cyber threats effectively.
Comprehensive Guide to the 50 Most Essential Windows Commands for Penetration Testers and Red Team Operators
Windows commands are essential tools for penetration testers and red team operators. Proficiency with these commands empowers effective reconnaissance, exploitation, privilege escalation, and more. In this comprehensive guide, we delve into the 50 most vital Windows commands, providing detailed explanations, command usage examples, and invaluable insights tailored for penetration testers and red team operators.
Comprehensive Guide to the 50 Most Essential Linux Commands for Penetration Testers and Red Team Operators
Linux commands constitute the fundamental toolkit of a penetration tester or red team operator. Proficiency with these commands empowers effective reconnaissance, exploitation, privilege escalation, and more. In this comprehensive guide, we delve into the 50 most vital Linux commands, offering detailed explanations, command usage examples, and invaluable insights tailored for penetration testers and red team operators.
Comprehensive Guide to Essential Skills for Aspiring Penetration Testers
n the realm of cybersecurity, ethical hacking—also known as penetration testing—is a vital practice that entails dissecting computer systems, networks, applications, and databases to uncover vulnerabilities. By simulating real-world cyberattacks, penetration testers identify weaknesses that could potentially be exploited by malicious hackers. This comprehensive guide serves as a beacon for aspiring penetration testers, equipping them with indispensable skills encompassing reconnaissance, vulnerability assessment, exploitation, post-exploitation, reporting, and endorsed certifications. Follow this guide to establish a robust foundation in ethical hacking and contribute to a safer digital landscape.